VPNs: What are they really? (And how VPN Service Providers Mislead and Confuse You)
- Robin Taylor
- Jul 29, 2025
- 8 min read
The term “VPN” has been tossed around quite a bit recently. Oftentimes you’ll find yourself being advertised to about some sort of VPN service through online content platforms, antivirus companies like Norton or McAfee, or targeted marketing from VPN service companies. While VPNs have their different use cases, unfortunately they are a commonly misrepresented technology as a way to up-sell their capabilities, set unrealistic expectations, or even outright lie about what they’re meant for. This is problematic, as it encourages some of the deceptive marketing practices surrounding our technologies today.
Before we get into it, however: what exactly is a VPN?
For those who don’t know, a VPN (virtual private network) is a special type of network setup that extends a private network, like an office network for example, virtually. They allow you to isolate or protect internet traffic, as well as allow devices to connect to a network without physically being there. For example, if you have a work laptop assigned to you by a company, they may require you to connect to their systems over the internet using a VPN if you need to access company data. If you open, download, or send data across this network, the network for that company will treat your transmissions as if you were at their location. Once you disconnect the VPN, you can no longer access their network. Depending on how the network is setup, different setups offer different methods of securing the traffic. These networks also have different strategies for how they can be configured.
The two common VPN strategies are ‘site-to-site’, and ‘remote’.
Remote setups are more specific to managing wandering devices, like laptops, home desktops, or phones. These devices are left in charge of establishing a connection to a network. Site-to-site setups are more specific to offices, branches, and businesses, in which these devices are able to communicate with each other through gateways (routers, firewalls, etc.) that are set up for this network.
VPN technology was first properly introduced by Microsoft’s Gurdeep Singh-Pall in 1996, who introduced Point-to-Point Tunneling Protocol (PPTP). Cisco later collaborated with Microsoft to improve the underlying security of PPTP by increasing encryption and accommodating different types of internet connections. Fast forwarding to the early 2000s, VPN services began to appear as a response to the growing presence of online businesses and personal internet usage, and by 2010, have become a critical asset to both individuals and companies as the internet became more relied upon for internet-based systems and communications.
VPN services and VPNs are two separate concepts despite their core functionality. VPN services are encrypted networks that are hosted by providers who have servers located in different parts of the world. When you connect to a VPN service, your traffic is forwarded to a select server, to which the server then takes your traffic and sends it out to the internet on your behalf, whilst returning encrypted traffic to you through the same server. As a result, you appear to be connected to a website or service from a different location in the world, and nobody but you and the service provider see the data sent and received. An additional benefit of this is that your public IP address or device IP address is masked to websites or services that are trying to identify you this way. It also allows you to bypass generalized censorship or access restriction attempts from governments or organizations, including geo-blocking.
Unfortunately, as a result of their growing popularity and commercialization, companies have misrepresented what these technologies are actually capable of lately. For example, while VPNs can be an added layer of security, it is only one layer. Your IP address, which is usually the main focus of marketing tactics, is also only one out of the many ways that your device can be identified. (For example, websites can use "cookies"—small text files stored on your device to remember your preferences and track visits—or "device fingerprinting," which identifies you based on unique details like your browser type, screen size, and installed fonts, even without an IP address.)
The most that an IP address exposes is the general location of where a device could be based on the geo-location of the network. VPN service providers, however, will overreach and claim that their services handle more than just this layer of security, exaggerate features, and have contradictions in their marketing. In addition to this, some service providers even have concerning terms, agendas, and privacy policies associated with their products which challenges their legitimacy and security claims.
Note: All of our examples in this article were taken from archived versions of website from July 27th, 2025, as well the official pages provided by service providers' websites. Links to these archives will be provided via Ghost Archive, who we are not sponsored by and is a third-party webpage archiving service. This article will primarily focus on ExpressVPN, Norton, Cyberghost, NordVPN, and McAfee’s products. While we intend to dive deeper into this topic in the future, other service providers will be acknowledged in another article.
Exaggeration of Protection of Information and Identity

ExpressVPN advertises that their VPN service “shields your identity” from services that want to track you. However, they do not acknowledge the limitations of VPNs. Multiple methods of tracking, including cookies, preference savings, persistent IDs, and tracking pixels exist on sites. (Preference savings store your site settings for convenience but can track habits; persistent IDs are unique codes tied to your account or device for long-term identification; tracking pixels are invisible images that log when you view a page or email.) A lot of other services claim the same thing as well.

ExpressVPN’s “What is VPN” explanation page also claims that VPN connections and tunnels “hide your internet activity from prying eyes, including hackers, internet service providers, and other third parties”. This is only partially true, as device fingerprinting and trackers can negate tunneling. In the modern day internet, it is still easy for bad actors to track you. On top of this, they also claim that “VPNs are an all-encompassing solution for protecting your online identity”. This is is false and is not an accurate representation of the security VPNs provide, which is setting a bad expectation of end-user security.


McAfee’s Safe Connect introductory and FAQ page sections claims that part of the information that is protected by their service is “banking account credentials and credit card information”. While this can be true for insecure networks, this is primarily hyperbolic, since this information is already protected by modern cryptography standards for online banking, including encryption that is provided by the HTTPS protocol. Modern web browsers also provide alerts and built-in functionality to warn you of a "man-in-the-middle" attack if it suspects one is in action.
Claims of Protection Against Malware, Phishing, and Scams

NordVPN claims that their VPN service helps “avoid phishing, scams, and malware”. While NordVPN themselves may add bonus functionality through software, VPNs themselves are not relevant to the prevention of malware, user engineering, and scam operations. This is another blatant up-sell for a technology that is not associated with this type of security. This also falls in line with conflating the definition of VPN, virus protection, and security awareness.
Conflating Definition of “VPN” With Other Products and Misleading Purchases

NordVPN is not the only one who is guilty of doing this. Norton is also conflating the definition of VPN by using it as a form of branding for other products. SurfEasy is the real name of their VPN service, but they have bundling plans called “Norton VPN”, which offers à la carte features not relevant to VPNs themselves. Norton VPN contains antivirus, “ai-powered scam detection software”, password managers, etc.
While you can purchase SurfEasy VPN by itself, it is only able to be done by subscribing to the NortonVPN standard plan.
Encouraging Abuse of Services and Piracy

Cyberghost promotes bypassing IP-based bans from games or services with their VPN service, which in turn promotes violating terms of services and ban-evading for platforms. If a user is banned for illegal activities and is being sold a product that encourages the evasion of end-user agreement terminations, this can be considered a legal issue. Often times, a user can have their agreement terminated and access to a service revoked due to some form of negative behavior such as cheating, hacking, communications abuse, or spam.
In addition to this, most VPN services also market their products to be used for bypassing regional locks for streaming content. This would fall under the description of encouraging piracy, which is considered a federal crime in the United States (though piracy is also considered to be a morally grey topic, which may be discussed in future articles).
Privacy Concerns
While there are many instances of privacy concerns that can be listed here, a rather interesting one that we will address is Norton's handling of public information regarding how they handle your data with their VPN service. Particularly, the issue lies in the lack of clarity, which is a common problem with majority of these services.

Norton claims to have a “no-logging” and zero-knowledge stance to their SurfEasy VPN service, which is supposedly further emphasized by being audited by their partner VerSprite, a cybersecurity firm. However, they later cloud their language surrounding the privacy of their service by having a clause in their Privacy Notice that states the service “collects data to monitor compliance of terms of service", as well "device identifier data", to which they keep it for up to 7 days if they determine “suspicious behavior” is detected or blocked.

They do not disclose specifically what data is tracked for compliance to terms of use beyond "frequency of abuse of services" for SurfEasy via. "data transfer sums" in their 'Data from our VPN backends' section of their Privacy Notice. Norton states that they have a readily available Transparency Report to prove the lack of information they have on their VPN users, but it does not provide any information regarding the results generated by their third-party auditing service directly beyond their No-Log Policy page. VerSprite has provided a letter of audit against Norton's VPN service in 2024, which in itself is a little vague in its findings. VerSprite claims that during their assessment of Norton's staged Edge servers, whom are responsible for the hosting of their VPN service, they found that "under certain conditions sensitive information could be logged which would certainly assist in identifying the VPN users" as part of the two identified potential privacy concerns.
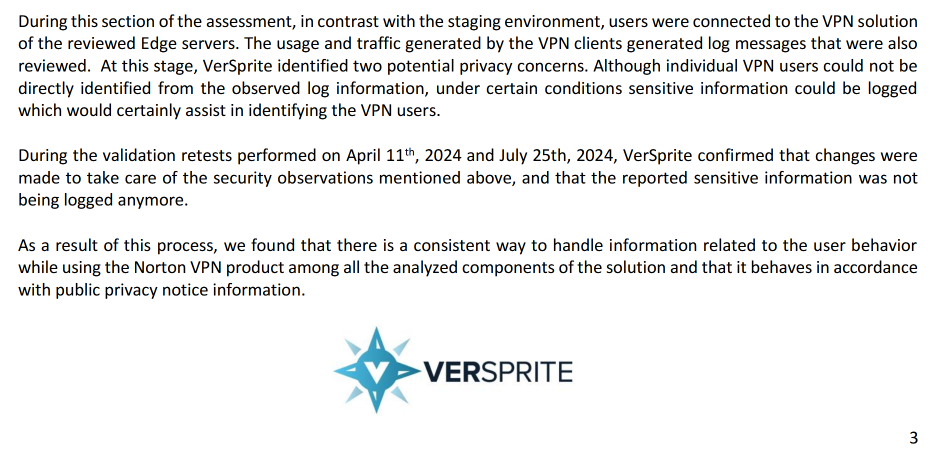
VerSprite does not publicly identify these conditions, nor do they mention what sensitive information could have been exposed as part of the audit letter for end-user awareness, even though they claim that Norton has since made corrections for these concerns. Because of the lack of transparency in these findings, the validity of the threat potential can be challenged.
While this is not something that can completely damage a user's experience with a VPN service like Norton's, this does raise the question on the amount of trust that can be placed in a product that can even belong to someone as big and notable as them. This is in addition to VPN service providers not mentioning the fact that they still have access to the traffic by being the receiver of your data despite their claims regarding their infrastructure. So while you are getting the benefits of masking traffic and their services, you are merely shifting your trust to another third-party and are subject to how they handle your information as a result. Some service providers do their best to protect you, but it is never guaranteed.
In a world where subscriptions or software as a service (SaaS) is becoming a more popular business model, there’s a lot of cloudy information, negative practices and inaccuracies in what our technology is meant to be used for in the race of buying and selling. When looking to leverage the benefits of a VPN service it’s best to be mindful of what is actually being advertised and stated by the service provider.
VPNs themselves are nothing more than a way for you to connect to a network, or website, from the outside with encryption. While we personally encourage you to use VPNs if you are connecting to an unknown network or are subject to government censorship, be aware of the limitations and risks involved. Do not believe in the marketing without doing your research. And know this: the best security is user knowledge and awareness!


Comments